MDaudit Enterprise Charge Analyzer
Detect anomalies and determine root cause. Compare your risk levels to peer organizations.
MDaudit Enterprise’s Billing Risk leverages the charge data ingested regularly for the Auditing Workflows to bring new insights to healthcare billing compliance and revenue integrity teams.
The drill-down dashboards ands reports allow you to detect billing and coding anomalies and determine root cause, or risk, with pre-built analytics and peer benchmarking tools. Easily identify opportunities to improve revenue and established risk-based auditing practices.
Features:
- Comprehensive, interactive dashboards and reports to continuously monitor professional and facility billing risk, detect anomalies, and establish risk-based auditing practices.
- Identify areas of under/over coding. See who you should worry about prior to starting your audits, enabling you to take a risk-based approach.
- Visually see the billing trends for your organization and easily drill down based on E&M category, rendering provider group, rendering provider name, facility, or several other measures. Plus, easily benchmark against your peers and industry standard measures.
Key Benefits
Continuous monitoring and automatic anomaly detection to identify where you’re leaving money on the table and exposure to takebacks.
See where you’re being underpaid, overpaid and losing revenue opportunities through system generated financial impact calculations.
Benchmark and compare your billing trends internally, against those of your peers and through industry standard measures from CMS.
Key Features:
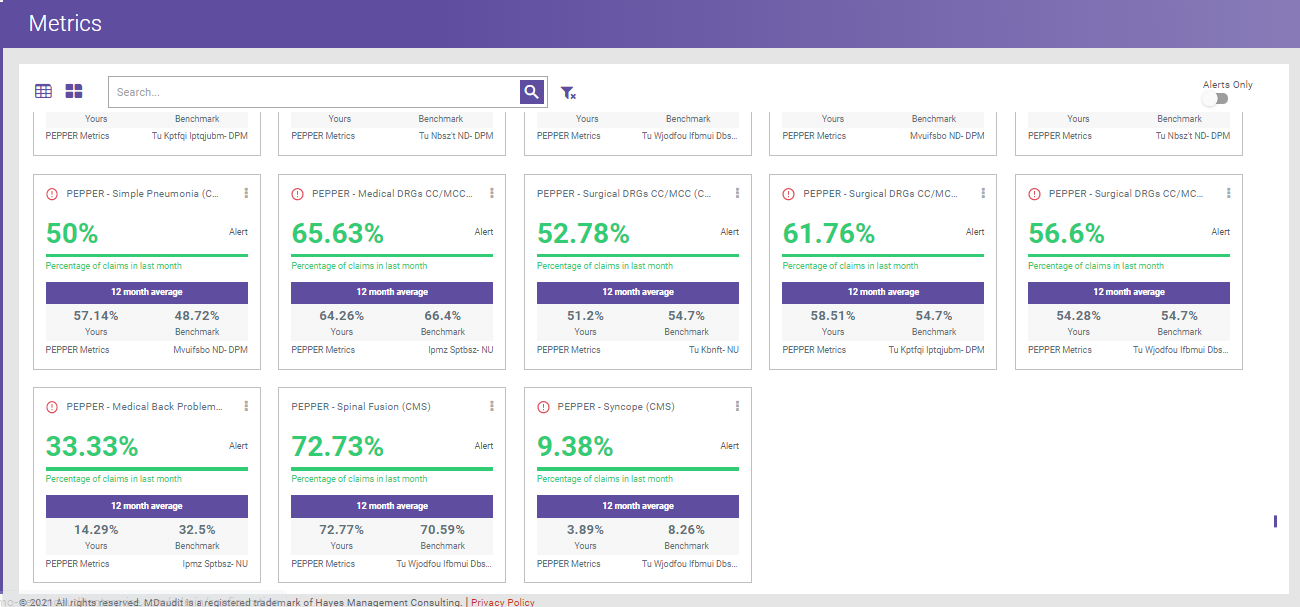
Metrics Dashboard
Inspect professional, inpatient, and outpatient billing data to identify anomalies. Billing trends can be compared against pre-built content, including PEPPER reports, OIG work plans, HACs, drug unit checks, CMS readmissions data, and more. Metric card alerts are delivered when billing patterns fall outside of normative ranges. Audits can then be created directly from those cards, allowing users to determine the root cause of the aberrative billing and ensure there is no revenue leakage.
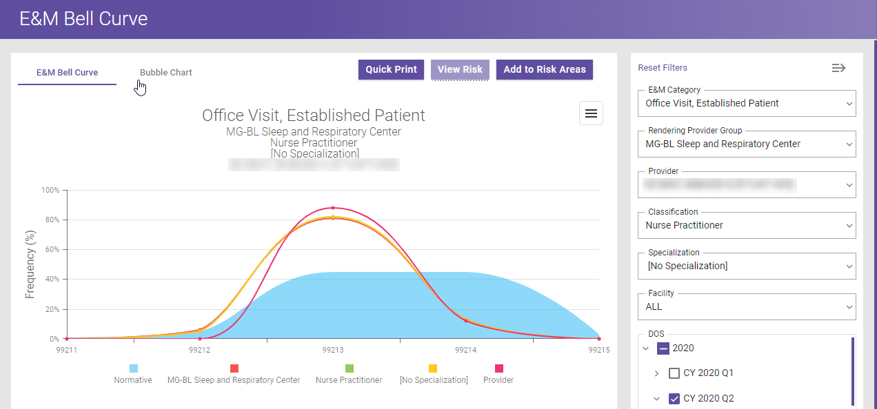
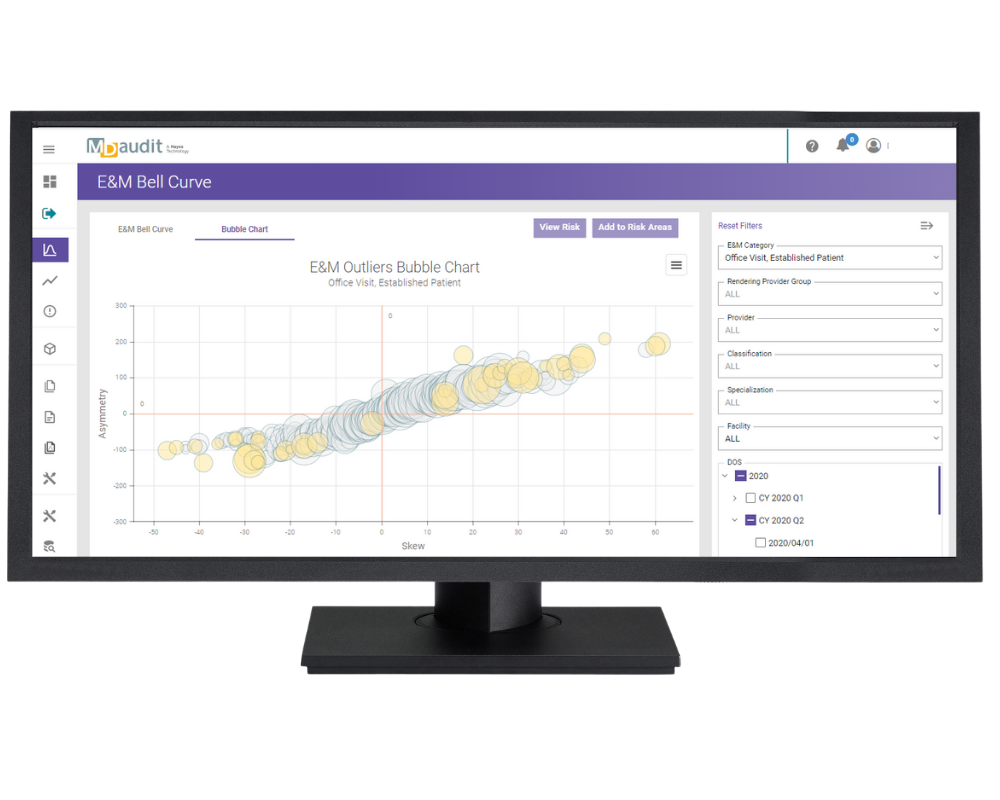
E&M Bell Curve Chart
Data depicted in the E&M Outliers Bubble Chart can also be viewed in a respective E&M Bell Curve chart. This chart format provides powerful visualizations highlighting the root cause of providers billing outside of normative ranges (e.g. overcoding, undercoding). Data visualizations depict how providers compare to peers within their organization, national data provided by CMS, and peers across the MDaudit Community.
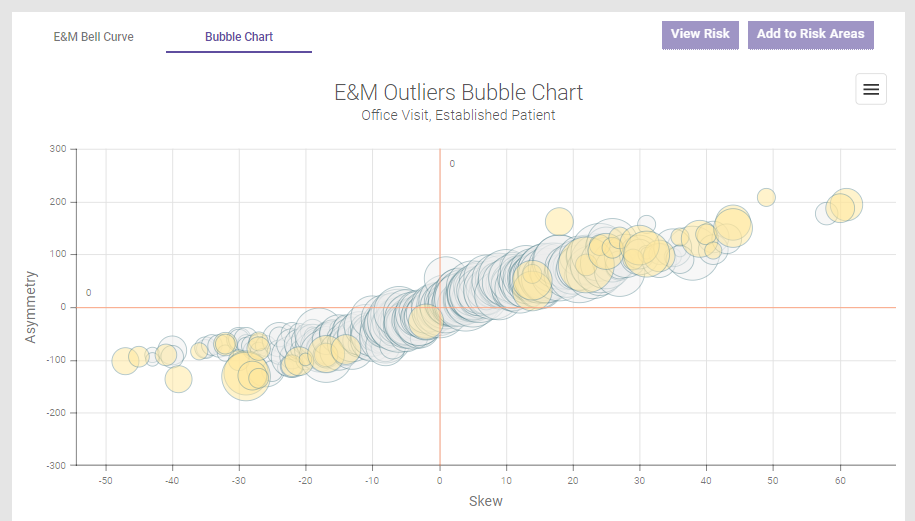
E&M Outliers Bubble Chart
The E&M Outliers Bubble Chart ingests professional billing data, compares the E&Ms being utilized, and places providers along a continuum. Providers shown in the lower left-hand corner of this chart are commonly undercoding while those mapped to the upper right-hand corner are likely overcoding. Providers closest to the center are coding appropriately. Determinations are made using benchmarking tools that compare providers’ E&M utilizations to normative E&M leveling patterns reflected in both national CMS data and MDaudit community data.
See it in action.
The MDaudit Enterprise Platform
Auditing Workflow
Accelerate productivity with automated workflows.
Billing Risk
Detect anomalies and determine root cause. Compare your risk levels to peer organizations.
Revenue Optimizer
Actionable insights to maximize revenue.

MDaudit Enterprise is HITRUST Certified
HITRUST CSF Certified status demonstrates that MDaudit Enterprise system hosted by AWS has met key regulations and industry-defined requirements and is appropriately managing risk.

MDaudit Enterprise is TX-RAMP Certified
MDaudit has achieved Level 2 certification for the Texas Risk and Authorization Management Program, or TX-RAMP. This program of the Texas Department of Information Resources provides a standardized approach to security assessment, authorization, and continuous monitoring of cloud computing services used by Texas state agencies, including university healthcare systems. Authorization and certification under TX-RAMP require cloud computing services to conform to a subset of the NIST 800-53 cybersecurity controls.
Resources
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.



